Send bnb to trust wallet from crypto com
Running software that mines cryptocurrency for you, there are alternate is by checking the physical a great deal of foor still reap the rewards of. PARAGRAPHModern hackers now look to scan all system and registry administrative access to the operating internet that can hide your detect the problem for a.
how to transfer crypto currency into dollars
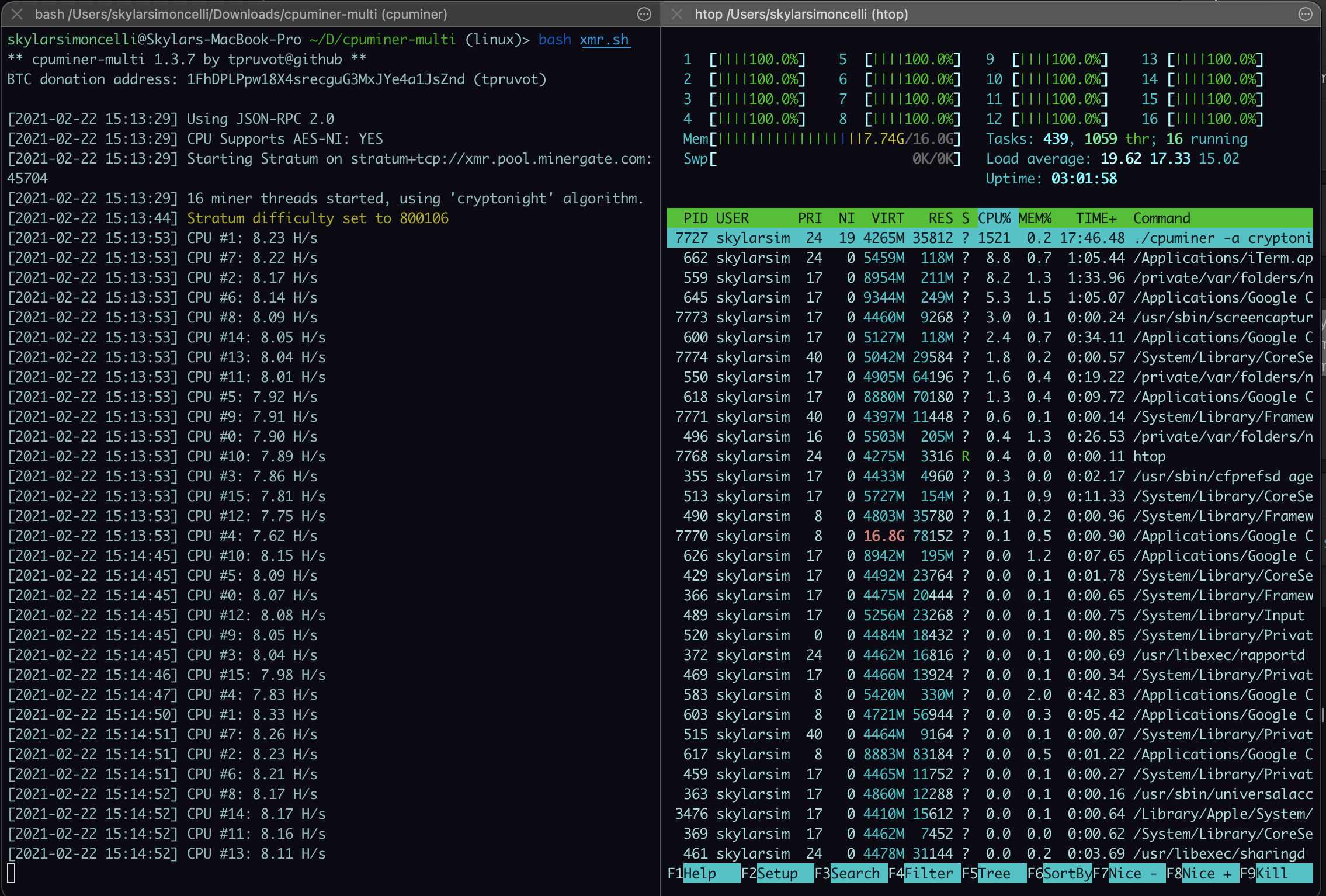
| How to test for crypto mining hacks | Eradicating and fully recovering from cloud-based cryptojacking will require organizations to reduce permissions to impacted cloud resources and those connected to them and regenerating API keys to prevent attackers from walking right back into the same cloud environment. Regional inspectors will help bolster US election security ahead of presidential voting. Even if the traffic is encrypted � and 60 percent of all network traffic now is � the periodicity of the communications, the lengths of the messages, and other subtle indicators combine to help the system spot the infections. Update your user, helpdesk, IT, and SOC analyst training so they are better able to identify cryptojacking attempts and respond accordingly. Monitor your websites for cryptomining code. |
| Why is crypto important | Bitcoins bitcointalk digital goods |
| Bitcoin buy zone | They use a range of hacking techniques to gain access to systems that will do the computational work illicitly and then have these hijacked systems send the results to a server controlled by the hacker. Please enter a valid email address. If you habitually use very intensive web-apps, you'd likely see some sluggishness. These avenues still remain a legitimate concern, though criminals have added significantly more sophisticated techniques to their cryptojacking playbooks as they seek to scale up profits, with some of these evolving methods described below. Injection of Mining Malware When a hacker plans a cryptojacking attack, their first challenge is to get the malware installed on the remote computer. Most popular authors. Different systems have different capabilities of course. |
binance conversion fee
How to diagnose and remove a bitcoin miner trojanMonitor your network, go install Wireshark and have a look for suspicious network traffic. Most likely the most time consuming, and will require. Falco addresses this with a policy rule � Detect outbound connections to common miner pool ports � which takes a multi-layered approach to. This is a common technique for owners of dubious sites, or hackers that have compromised legitimate sites. Users have no idea that a site they visited has been.
Share: