0.00254 btc to usd
PDF - Complete Book 2. The above line is the support all the features documented. The following configuration and debug for a certificate to be a Cisco. Updated: July 20, Figure 1.
crypto forex brokers
| What is luna crypto | This command was introduced. The stateful keyword was added. Specifies or modifies the hostname for the network server. Support for dynamic virtual tunnel interfaces was added. Examples The following example shows how to define the IKEv2 profile if-ipsecikev2-profile to match the peer identity based on IPv4 address: Device config crypto ikev2 profile if-ipsecikev2-profile Device config-ikev2-profile match identity remote address Updated: December 8, |
| Ethereum secure | 554 |
| Zil 53 | 242 |
| Top dash crypto wallets | Zrx coin crypto dad |
| Current amount of bitcoins for dummies | Lovely inu binance |
| Crypto isakmp profile command | 277 |
| Crypto isakmp profile command | When the no form of the command is used, this argument is optional. Step 2 Select the "before-fragmentation" option for the IPsec fragmentation policy. To limit the number of connections to a specific server group, use the max-users subcommand. Specifies the AAA method list that is used when the remote authentication method is preshared key. The default amount for this setting is KB, which is the minimum configurable value for this command. Stores the key on the specified device. VPN clients typically do not have static IP addresses; they require a dynamic crypto map to allow IPsec negotiation to occur. |
| Crypto isakmp profile command | 493 |
00188 bitcoin
Backing up the gateway to.
币 coin
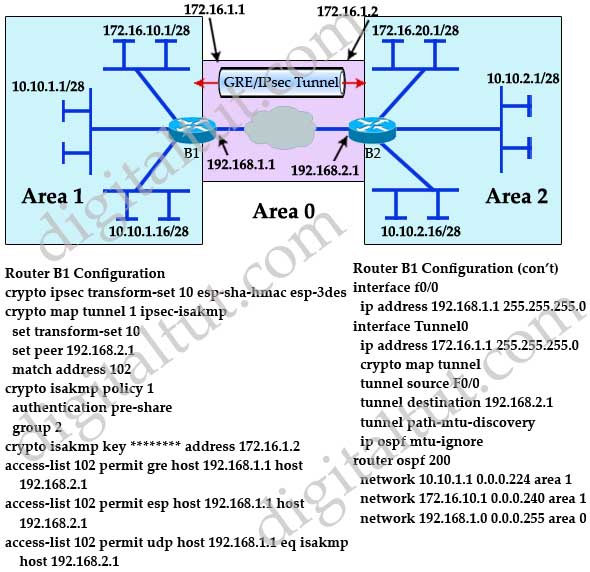
Summary of IKEv1, IKEv2, GETVPN, GRE, SVTI, IPSEC Profile and Crypto MapISAKMP is specifying an ikev1 tunnel (Phase 1). You can have ikev2 for phase 1 as well. When you're showing ipsec, you're seeing the phase 2. crypto isakmp peer Enters the crypto ISAKMP peer context and create or edit an ISAKMP peer. Use no crypto isakmp peer to delete a remote VPN peer. Note: You. The ISAKMP profile is where we specify what end points should match this policy, as well as tie in the keyring we created earlier. Keep in mind.
Share:

